Author: Hal Stern
University of California, Irvine
December 2025
Cybercrime has emerged as a major threat to individuals and companies. Consumers are regularly notified of security breaches that put their personal data, including social security numbers, at risk. Ransomware attacks have impacted universities, medical centers and companies of all types. Understanding cybercrime and the effectiveness of anti-cybercrime measures requires the ability to measure the frequency and severity of incidents. This has proven challenging for several reasons. For one thing, not all cybercrime is reported because individuals may not know they have been victimized and, even if they do realize, it is not obvious where to report it. It is also challenging to know how to count cybercrime incidents – is a breach impacting a million customers a single crime with a million victims or multiple crimes. One surprising reason that it is so difficult to study cybercrime is that existing crime reporting systems are not well equipped to handle such incidents.
The primary crime reporting system in the United States is the FBI’s National Incident-Based Reporting System (NIBRS). However, NIBRS includes only two explicit forms of cybercrime as incidents that can be reported, identity theft and hacking/computer invasion (both added in 2014). There are two other data items associated with each reported crime that can be used to indicate the involvement of computer technology in the commission of a crime. There is a data item (data element 8) that is used to denote other factors impacting the incident. The element allows the reporter to note “offender suspected of using …” with response options that include drugs, alcohol, or computer equipment. The data element for location of crime (data element 9) was modified in 2014 to include cyberspace as a possible location for a crime. These changes to NIBRS have made it possible to register cybercrime but it is not very convenient. For example, one can report a ransomware attack as a blackmail or extortion incident with offender suspected of using computer equipment and a location of cyberspace but does not appear to be common at this time.
The absence of reliable data led Congress to pass the Better Cybercrime Metrics Act requiring the FBI to add cybercrime statistics to NIBRS and the Bureau of Justice Statistics (BJS) to add cybercrime to their National Crime Victimization Survey (NCVS). The Act also required the Department of Justice to work with the National Academies of Science, Engineering and Medicine to convene a panel of experts to support the FBI and BJS in meeting the requirement. Specifically, the panel was asked to develop a taxonomy for cybercrime and make recommendations for the use of the taxonomy in NIBRS and NCVS. (In the interest of full disclosure, I served as chair of the committee.) The panel, in its report, “Cybercrime Classification and Measurement”, available at the National Academies Press, developed a taxonomy (see figure below) that identifies crimes based on the degree of computer involvement (e.g., crimes that can only happen with computers versus crimes that are enabled or enhanced by computers) and by the nature of the criminal acts (acts targeted against machines/data, acts of fraud, acts against individuals, etc.). The panel recommends that in the future every crime report in NIBRS should include a required field that identifies the degree of cyber involvement using the developed taxonomy.
Such a change would require a significant redesign of NIBRS (or NCVS), so the panel also made a number of recommendations that can be implemented more quickly that would enhance our ability to study cybercrime – these include enhancing documentation and training to make sure that the existing NIBRS tools (i.e., the available crimes and the relevant data elements) are used more regularly.
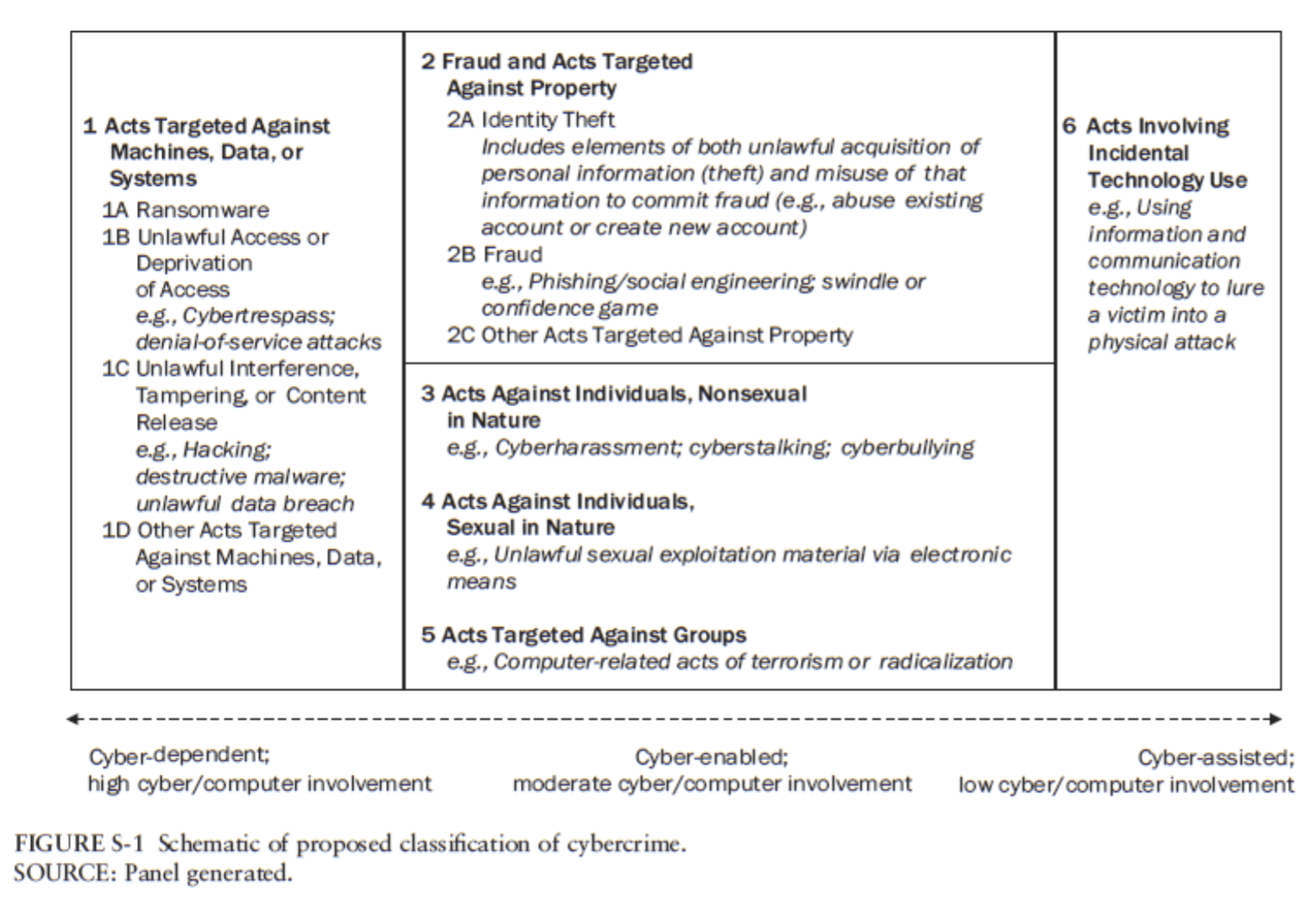
From Cybercrime Classification and Measurement, National Academies Press, 2025.